Digital Sovereignty isn’t a switch you flip

Is ‘Sovereignty’ becoming a buzzword?
Digital sovereignty is making headlines, especially in Europe. Concerns about US hyperscalers and political influence are driving a push toward local cloud providers.
Oversimplifying sovereignty as an on/off switch leads to poor decisions.
Let’s ground the discussion in what sovereignty really means.
What does Sovereignty really mean?
Sovereignty implies total control. Over your hardware, software, infrastructure, data, and governance.
But in the real world, full control is rare and expensive.
Most organizations don’t need 100% sovereignty. What they need is partial sovereignty: a strategic, risk-based approach that reduces critical dependencies without overengineering the rest.
That might look like:
- Ensuring direct control over identity systems, encryption keys, and where data resides
- Isolating critical workloads from foreign jurisdictions or shared control planes
This is sometimes called strategic autonomy. And it comes with real trade-offs:
- Full control vs. speed
- Best-of-breed tools vs. slower, in-house alternatives
- Lower risk exposure vs. higher cost
- Long-term flexibility vs. short-term simplicity
- Control vs. your team’s capacity to manage it
Choosing sovereignty means making hard calls. Not checking a compliance box.
Most organizations will land somewhere in the middle. Adopting sovereignty gradually where it matters most.
Sovereignty isn’t all or nothing. It’s built on choices
Digital sovereignty isn’t binary. It’s not something you have or don’t have. It’s shaped by the trade-offs you make and by how much control you retain in the areas that matter most.
Governance gets most of the attention. But the next five aspects are often overlooked, and they matter just as much.
1. Governance: Who sets the rules?
Most conversations about digital sovereignty start and end with governance.
Legal jurisdiction, contractual power dynamics, and geopolitical exposure are real concerns. The US CLOUD Act, terms of service that can change overnight, and providers tied to foreign policy all raise valid sovereignty flags.
But sovereignty isn’t just about who writes the rules. It’s about whether you can enforce them. That’s where identity, infrastructure, and cybersecurity enter the picture.
2. Identity: Who really holds the keys?
Identity is power. It’s the front door to everything.
If someone else controls your identity provider, they control who gets in. That’s not just a security risk. It’s a sovereignty risk.
Most enterprise organizations rely on US-based identity providers like Microsoft Entra ID, Okta, Google Workspace Identity, or Auth0. These services are tightly integrated into business workflows, and self-hosting alternatives are rarely feasible at scale.
This makes identity one of the hardest areas to localize or decouple. Even when security is strong, jurisdictional control remains out of reach if the identity provider operates under foreign legal frameworks.
Ask yourself:
- Is your identity system hosted abroad?
- Who issues your access tokens and trust anchors?
- Can external actors suspend or reset accounts without your involvement?
Sovereignty in identity means managing what most delegate. More control, but also more responsibility.
Too often, identity is treated as background infrastructure. But in reality, it’s the central gatekeeper to sovereignty.
3. Cloud: Innovation or independence?
Cloud isn’t just about buying compute, it’s about joining an ecosystem.
Hyperscalers offer unmatched velocity. AI services, serverless compute, global scalability, and seamless DevOps pipelines all tightly integrated and ready to deploy. They also provide access to a massive marketplace of independent software vendors: thousands of third-party services from companies like Databricks, SAP HANA, Elastic, Snowflake, and HashiCorp. These cover data processing, analytics, observability, compliance, and infrastructure management.
But that convenience comes with trade-offs. The deeper you embed, the harder it becomes to move.
Cloud vendor lock-in isn’t a bug. It’s a business model.
Sovereign clouds, on the other hand, often lag behind. Fewer features. Slower release cycles. Limited automation. That makes innovation harder and teams slower.
The cloud offers real advantages, so much so that it’s easy to embrace without pause. But sovereignty isn’t about avoiding the cloud. It’s about using it with intention. That means understanding what you’re building on, what you’re locking into, and where you still need control.
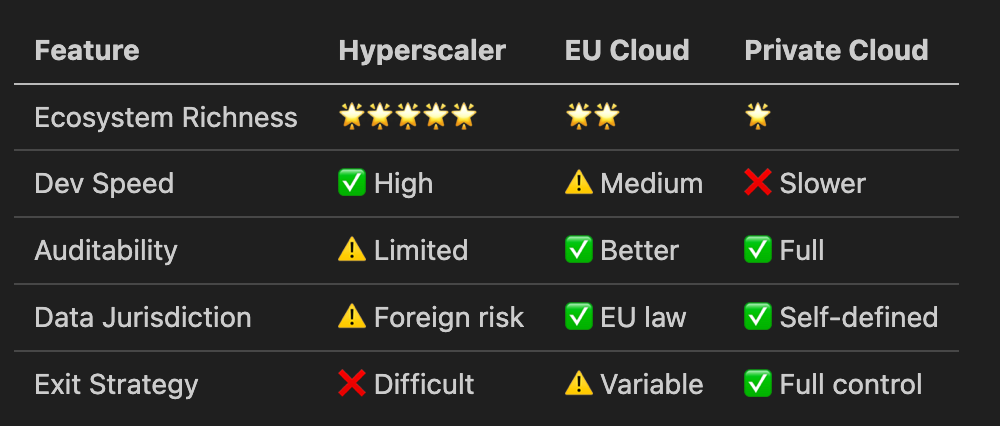
Choosing a platform means choosing your trade-offs. Do you want innovation speed now, or optionality later?
4. Data and Applications: More than storage
Sovereignty isn’t just about where your data is stored. it’s about how it’s handled, who processes it, and whether you maintain control from end to end.
Data at rest doesn’t mean data at peace.
You need answers to questions like.
- Where does your data and telemetry live?
- Who processes and analyzes it?
- Do you own and manage your encryption keys?
- Are your apps portable or locked to a vendor?
Sovereignty Signals
- Ownership: You govern classification and lifecycle
- Residency: Data and telemetry stay local
- Processing: No foreign SaaS for sensitive workloads
- Encryption: You own the keys
- App Design: Transparent and controlled
- Analytics: In-house or governed
- Portability: No lock-in barriers
- Shadow IT: Centrally monitored
Especially Shadow IT is a growing risk to sovereignty. Even with strong policies, users often bypass controls. Generative AI tools like ChatGPT make this worse. Employees may paste confidential data into unapproved platforms without realizing the consequences.
If your critical data flows into systems outside your control, it's no longer sovereign.
Data isn’t sovereign just because it's stored in your environment. It’s sovereign when you control its entire journey. From storage to processing to deletion.
5. Endpoints: The weakest link
Your cloud might be sovereign but what about the devices that access it?
Sovereignty ends where endpoint control stops.
Even Linux distributions commonly used in enterprise environments often rely on US-based companies for maintenance, security updates, or enterprise support. Red Hat, Canonical, and others may operate globally but are subject to US regulations or business dependencies.
This means that even when choosing open-source platforms, endpoint sovereignty can still be compromised through upstream control or vendor reliance.
Questions to ask:
- Who builds and signs the operating system?
- Where does its telemetry go?
- Is your MDM (Mobile Device Management) control plane based in another country?
- Can a foreign provider revoke access or push updates?
You can harden your cloud, but if you ignore the endpoints, you’re still exposed.
Linux-based endpoints and local MDM tools provide more control. But adoption takes effort.
Sovereignty travels with the user. If the edge isn’t secure, your sovereignty isn’t either.
6. Security Foundations: Control requires defense
This might be the most overlooked part of the entire conversation.
There is no digital sovereignty without cybersecurity. Sovereignty without defense is like owning a house with broken locks.
We talk a lot about governance and control. but if your systems can be breached, monitored, or manipulated, you may own them, but you don’t control them.
That’s especially dangerous for SMEs. Many already struggle to manage security operations. alert fatigue, patch delays, limited detection engineering. Moving to a sovereign setup means taking on even more security responsibility without the resources of a hyperscaler to back it up.
Meanwhile, ransomware-as-a-service has become a business model for cybercrime syndicates. Every time SMEs weaken their defenses, these groups grow stronger. It’s not just a company-level risk. it’s a national resilience issue.
More control also means more responsibility for detection, response, and continuous defense.
Here’s what that trade-off often looks like
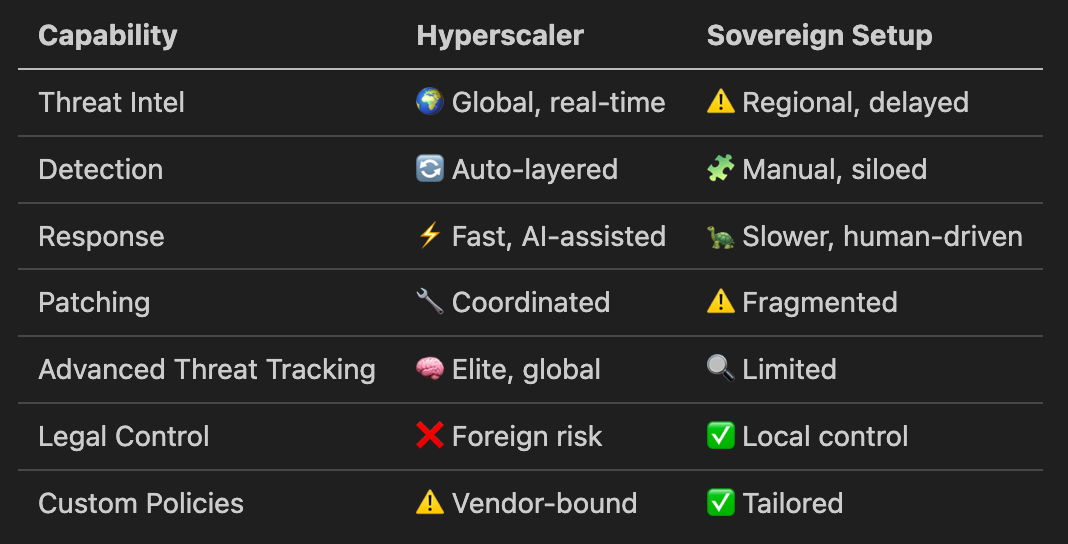
Security is the foundation of sovereignty not the finishing touch.
If you're an SME exploring sovereignty, start by strengthening your detection and response capabilities before taking on full security operations. Full sovereignty may never be viable, but selective autonomy in sensitive areas can still reduce risk without overextending.
Final reflection
The more control you gain, the more sovereign you become, but also the more complexity you take on.
Sovereignty is a trade-off. Not a checkbox, not a marketing claim, and definitely not a switch you flip.
So where is your sovereignty most vulnerable? Which controls reduce real risk, and which only slow you down?
Sovereignty isn’t an end state. It’s a posture. One worth rethinking. Especially now.